Introduction Conditional Access
If you are using VMware Workspace ONE Access as your Primary Identity Provider in your organisation, you already have the option to provide a smooth Conditional Acces integration with Workspace ONE UEM. Sascha Warno explains this very well in one of his Conditional Access video's:
I suggest to check out his article on VMware TechZone:
https://techzone.vmware.com/resource/compliance-integration-ms-office-365-using-workspace-one-access
Azure AD Conditional Access
For multiple reasons your organisation could require Azure Active Directory as the Primary Identity provider for authentication etc. In this article i want to share some details about the integration of Azure AD Conditional Access with VMware Workspace ONE UEM for macOS devices:
Already over a year ago VMware announced the capability of providing Conditional Access with macOS to Azure AD:
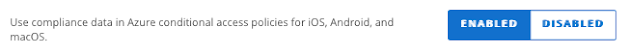
Besides macOS, support is currently for Windows, iOS and Android.
Requirements that needs to be in place for macOS are:
- Workspace ONE Intelligence
- Valid subscription to Microsoft Intune assigned to users
- Azure AD integration with Workspace ONE UEM
- macOS, require Workspace ONE Intelligent Hub 21.11 higher
- Workspace ONE UEM Console version 21.11 or higher
Configuration
After the requirements are met, Azure AD Conditional can be enabled in Workspace ONE UEM in Groups and Settings -> Directory Services. Please note that this will also enable it for iOS and Android.
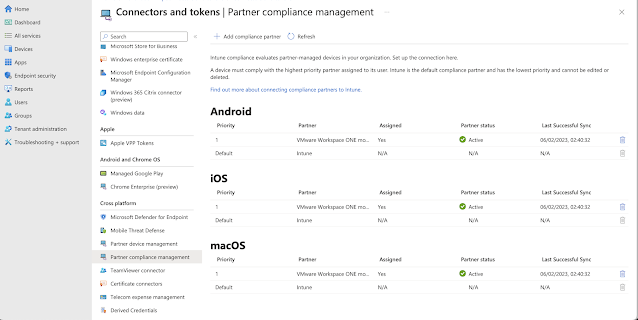
After the configuration is successful, you will see the configuration under Partner Compliance management in Intune:
Register macOS to Azure AD:
Because macOS doesn't support Azure AD join, the device is probably not registered yet in Azure AD.
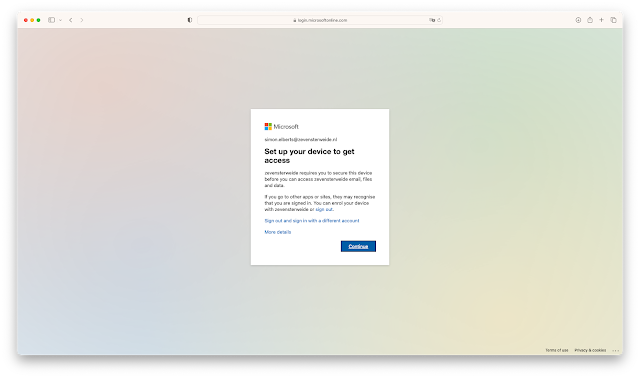
The user will need to register the device the first time it authenticates through an Azure AD federated app with Conditional Access enabled. If configured correctly, the user will be prompted to register through the Workspace ONE Intelligent Hub:
After hitting the continu button in the above scree. The user will be redirected to the below page:
Because it is macOS, both iPad and macOS Hub will be visible. To register, the user will need to click on the 'Connect Now' button in the page. This will redirect to the Intelligent Hub and if succesfull, the device will be registered in Azure AD under devices:
- If successful registered, the MDM under de device will show 'Microsoft Intune' as this is the Compliance manager.Azure AD Conditional Access Policy:To prompt the user for conditional acccess, you will need an Conditional Access policy in Azure AD. In Azure AD go to -> Security -> Conditional Access and create a new policy:Make sure that for testing purposes you assign the policy only to a certain application and/or user base, so you are not locking out any users. In this example i have assigned my test user to Office 365 application:
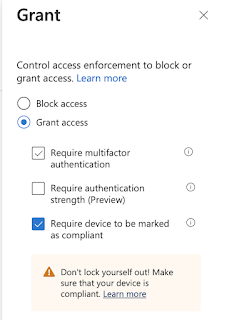
Under 'grant' require the device to be marked as compliant:




Comments
Post a Comment